Create a KMS configuration
Encryption at rest uses a master key to encrypt and decrypt universe keys. The master key details are stored in YugabyteDB Anywhere in key management service (KMS) configurations. You enable encryption at rest for a universe by assigning the universe a KMS configuration. The master key designated in the configuration is then used for generating the universe keys used for encrypting the universe data.
Encryption at rest in YugabyteDB Anywhere supports the use of CipherTrust KMS.
EA
CipherTrust support is Early Access. To enable the feature in YugabyteDB Anywhere, set the Allow CipherTrust KMS Global Runtime Configuration option (config key yb.kms.allow_ciphertrust) to true. Refer to Manage runtime configuration settings. Note that only a Super Admin user can modify Global configuration settings.
CipherTrust Manager prerequisites
You must have a running CipherTrust Manager installation, and it must be accessible to YugabyteDB Anywhere.
To create a KMS configuration, you need either the credenials of a CipherTrust user, or an authentication token.
-
You can use a normal local user, or an LDAP-based user.
The user or group that your user belongs to requires the following Key Access Properties:
- Read
- Use
- Encrypt
- Decypt
For more information on managing users, refer to the CipherTrust Administration documentation.
-
If you use refresh tokens to authenticate, when the token expires you need to manually update the KMS configuration with the new token. For information on using authentication tokens, refer to Authentication tokens in the CipherTrust documentation.
To use a pre-existing CipherTrust key, the key must have the following properties:
- It must be Active.
- Have the following Key Usage Permissions:
- Encrypt
- Decrypt
YugabyteDB Anywhere can also create a CipherTrust key with the correct settings when creating a KMS configuration.
Create a KMS configuration
You can create a KMS configuration that uses CipherTrust, as follows:
-
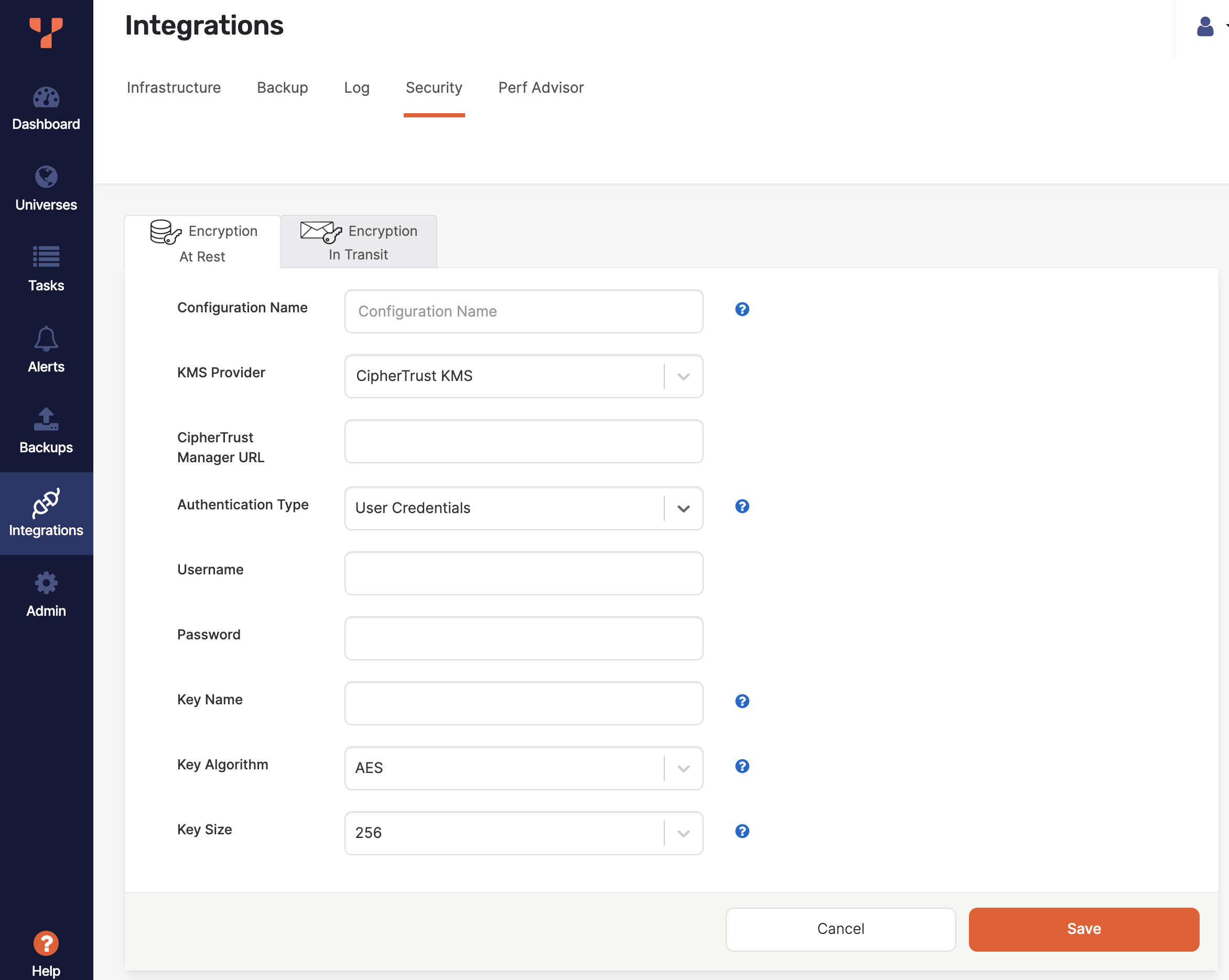
Navigate to Integrations > Security > Encryption At Rest to access the list of existing configurations.
-
Click Create New Config.
-
Enter the following configuration details in the form:
- Configuration Name — Enter a meaningful name for your configuration.
- KMS Provider — Select CipherTrust KMS.
- CipherTrust Manager URL — Enter the URL of your CipherTrust Manager deployment. This URL must be accessible to your YugabyteDB Anywhere instance.
- Authentication type — Choose User Credentials to provide a username and password, or Refresh Token to provide a token.
- Key Name — Enter the name of the key. If a key with the same name already exists, the existing key is used; otherwise, a new key is created automatically using the specified algorithm and size.
- Key Algorithm — Choose the encryption algorithm to use to create a new key.
- Key Size — Choose the key size for a new key.
-
Click Save.
Your new configuration should appear in the list of configurations.
-
Optionally, to confirm that the information is correct, click Show details. Note that sensitive configuration values are displayed partially masked.
Modify a KMS configuration
You can modify the credentials to use to access your CipherTrust Manager as follows:
-
Navigate to Integrations > Security > Encryption At Rest to open a list of existing configurations.
-
Find the configuration you want to modify and click its corresponding Actions > Edit Configuration.
-
Provide new values for the Authentication fields.
-
Click Save.
-
Optionally, to confirm that the information is correct, click Show details or Actions > Details.
Delete a KMS configuration
Note
Without a KMS configuration, you would no longer be able to decrypt universe keys that were encrypted using the master key in the KMS configuration. Even after a key is rotated out of service, it may still be needed to decrypt data in backups and snapshots that were created while it was active. For this reason, you can only delete a KMS configuration if it has never been used by any universes.To delete a KMS configuration, click its corresponding Actions > Delete Configuration.